- Encryption: All data sent through the tunnel is encrypted.
- Bypass firewalls: SSH tunnels can allow access to remote services behind firewalls that do not openly expose the required ports.
- Access control: You can control exactly who can access your database by managing SSH tunnel users and keys.
- Network isolation: SSH tunnels can help isolate your network traffic from the public internet.
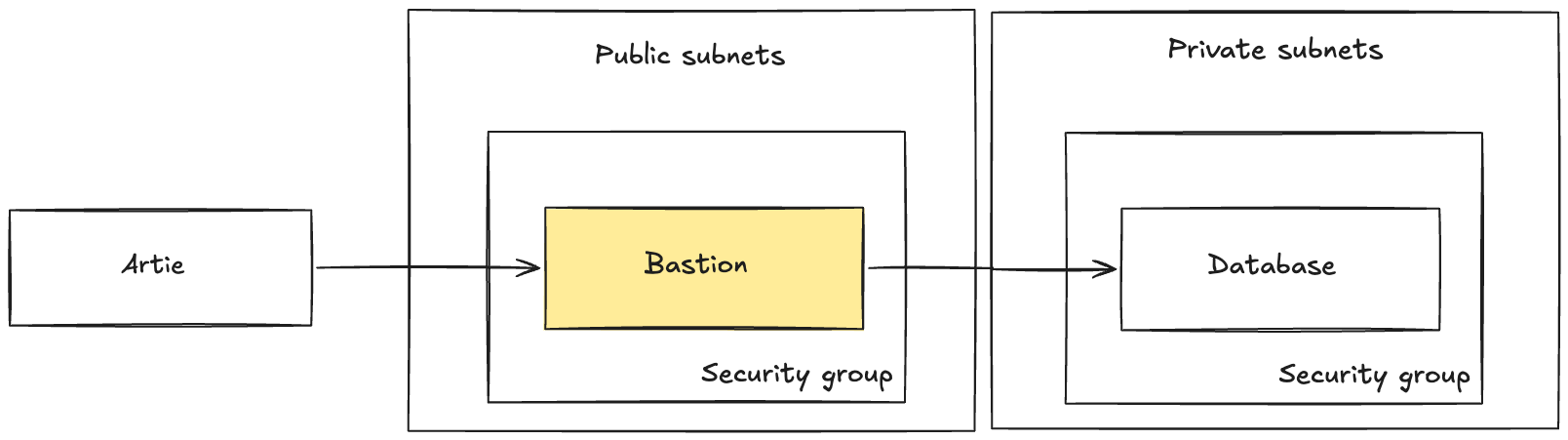
How to set up an SSH tunnel
- Create a new EC2 instance (or equivalent).
- Record the public IP address and port.
- Go to Settings > SSH tunnels tab and click
New SSH tunnel. - Copy the public IP address and port from step 2 and click save.
- Copy the public key and add this to
~/.ssh/authorized_keyson your SSH tunnel